The threat actor known as SideWinder has added a new customized tool to its arsenal of malware being used in phishing attacks on Pakistani public and private entities.
“Phishing links in emails or posts that mimic legitimate messages and services from government agencies and organizations in Pakistan are primary attack vectors for the gang,” Singapore-headquartered cyber-security group Group-IB said in a Wednesday report.
SideWinder, also known as Hardcore Nationalist, Rattlesnake, Razor Tiger and T-APT-04, has been active since at least 2012, focusing primarily on Pakistan and other Central Asian countries such as Afghanistan, Bangladesh, Nepal, Singapore and Sri Lanka.

Last month, Kaspersky attributed to this group over 1,000 cyber attacks that took place in the last two years, calling it its persistence and sophisticated blurring techniques.
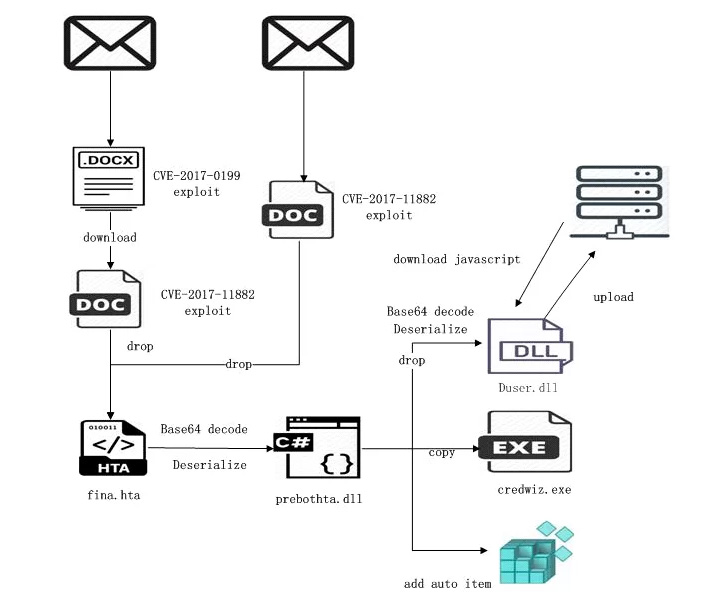
The threat operandi modus operandi involves the use of spear-phishing e-mails to distribute malicious ZIP archives containing RTF or LNK files that download an HTML application (HTA) payload from a remote server.
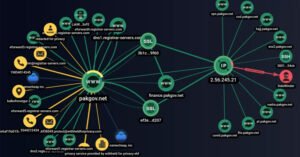
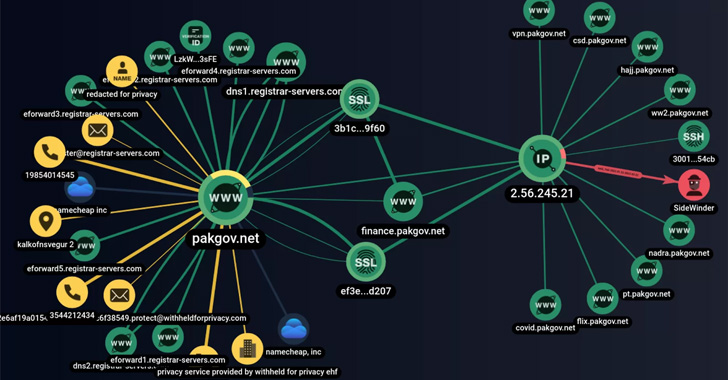
This is accomplished by embedding fraudulent links designed to mimic legitimate messages and services from government agencies and organizations in Pakistan, where the group also creates similar websites that act as government websites to harvest user information.
The custom tool identified by Group-IB, called SideWinder.AntiBot.Script, acts as a traffic guidance system that redirects Pakistani users who click on phishing links to junk domains.
Should a user whose client’s IP address differs from Pakistan’s click on the link, the AntiBot script redirects to an authentic document located on a legitimate server, indicating an attempt to geofence its targets.

“The script checks the client browser environment and decides, based on multiple parameters, whether to issue a malicious file or redirect to a legitimate resource,” the researchers said.
Of particular mention is a phishing link that downloads a VPN application called Secure VPN (“com.securedata.vpn”) from the official Google Play Store in an attempt to emulate the legitimate Secure VPN app (“com. securevpn.securevpn “).
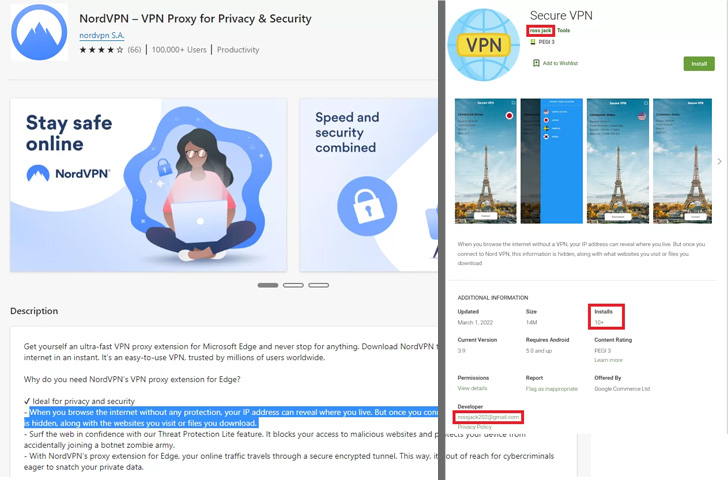
While the exact purpose of the fake VPN app remains unclear, this is not the first time SideWinder has sneaked past Google Play Store protection to release junk apps under the guise of help software.
In January 2020, Trend Micro detailed three malicious apps disguised as photography and file management tools that exploited a security flaw in Android (CVE-2019-2215) to gain root privileges as well as abuse access service permissions to collect sensitive information.