
Getty Images
Vulnerabilities recently discovered by Microsoft make it easy for people who have a grip on many Linux desktop systems to quickly get root system privileges – the latest extension of privilege flaws that have emerged in the open source operating system.
As operating systems have been hardened to resist compromises in recent years, privilege elevation vulnerabilities (EoP) have become a crucial ingredient for most successful hacks. They can be exploited along with other vulnerabilities, which in themselves are often considered less serious, with the latter providing what is called local access and the former escalating root access. From there, opponents with physical access or limited system privileges can implement backdoors or execute code of their choice.
Nimbuspwn, as Microsoft has called the EoP threat, are two vulnerabilities found in the networkd dispatcher, a component of many Linux distributions that send network status changes and can run various scripts to respond to a new status. When a machine starts, networkd dispatcher runs as root.
Microsoft
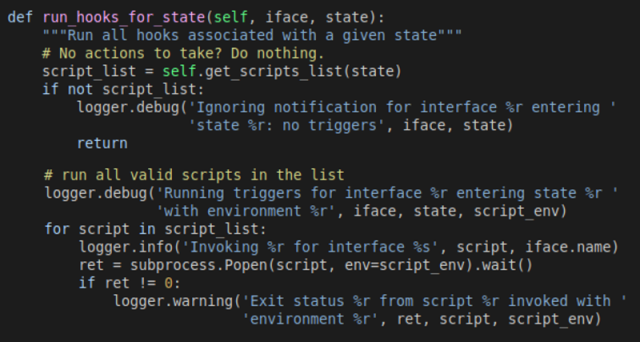
The bugs, tracked as CVE-2022-29799 and CVE-2022-29800, combine threats, including directory review, symlink race, and time-of-check time-of-use (TOCTOU) race mode. After reviewing the Networkd Dispatcher source code, Microsoft researcher Jonathan Bar Or noted that a component known as “_run_hooks_for_state” implements the following logic:
- Detects the list of available scripts by invoking the “get_script_list” method, which calls a separate “scripts_in_path” method, which is intended to return all the files stored in “/etc/networkd-dispatcher/.d”- folders.
- Sorts the script list
- Runs each script with the process subprocess.Popen and delivers custom environment variables
Microsoft
Run_hooks_for_state leaves Linux systems open for directory-traversal vulnerability, designated as CVE-2022-29799, because none of the functions it uses purifies the modes used to build the correct script path from malicious input. Hackers can exploit the vulnerability to break out of the “/ etc / networkd-dispatcher” root directory.
Run-hooks_for_state contains a separate bug, CVE-2022-29800, which leaves systems vulnerable to the TOCTOU run mode, as some time elapses between scripts being detected and being executed.
Opponents can exploit this latter vulnerability to replace scripts that networkd dispatchers believe are rooted with malicious ones of their choice. To ensure that Linux executes the hacker-supplied malicious script instead of the legitimate one, the hacker plants multiple scripts until one finally succeeds.
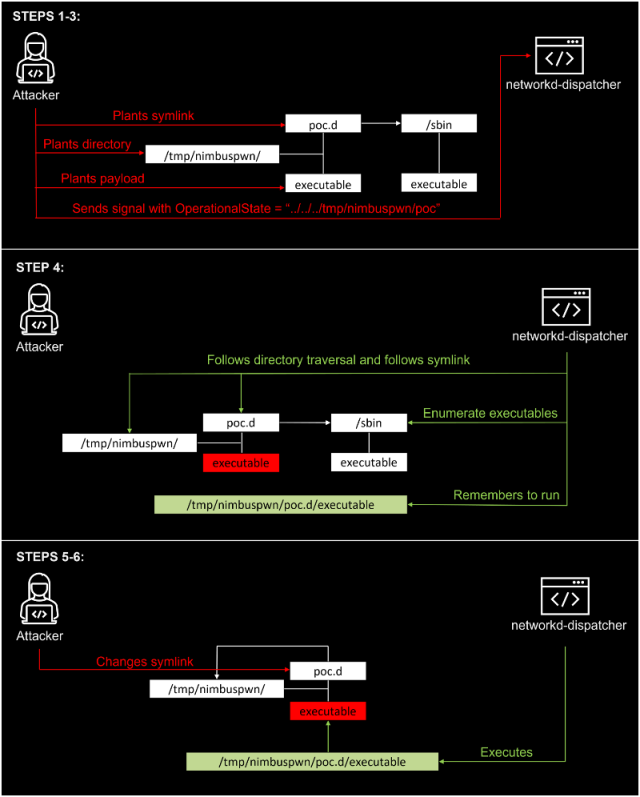
A hacker with minimal access to a vulnerable desktop can link exploits to these vulnerabilities that provide full root access. The utilization flow looks like this:
- Prepare a folder ”/ tmp / nimbuspwn“and plant a symbol link”/tmp/nimbuspwn/poc.d“to point to”/ sbin”. That “/ sbin” the directory was chosen specifically because it has many executable files owned by root that do not block if run without further arguments. This will abuse symbolic race problem we mentioned earlier.
- For each executable filename under “/ sbin“Owned by root, plant the same filename under”/ tmp / nimbuspwn”. If e.g./ sbin / vgs“is executable and owned by root, plant an executable file”/ tmp / nimbuspwn / vgs”With the desired payload. This will help the attacker win the race mode imposed by TOCTOU vulnerability.
- Send a signal with Operational mode “../../../tmp/nimbuspwn/poc”. This abuses directory review vulnerability and escapes the script directory.
- The Networkd-dispatcher signal handler starts and builds the script list from the directory “/Etc/networkd-dispatcher/../../../tmp/nimbuspwn/poc.d”which is actually the symbol link (“/tmp/nimbuspwn/poc.d”), which points to “/ sbin”. Therefore, it creates a list composed of many executable files owned by root.
- Quickly change the symbol link “/tmp/nimbuspwn/poc.d “ to point to “/ tmp / nimbuspwn”. This abuses TOCTOU race mode vulnerability – the script path changes without networkd-dispatcher be alert.
- The sender starts running files that were originally under “/ sbin“but in truth below”/ tmp / nimbuspwn” library. Since the sender “thinks” that these files are owned by root, it executes them blindly with subprocess.Popen as root. Therefore, our attacker has successfully exploited the vulnerability.
Here is a visualization:
Microsoft
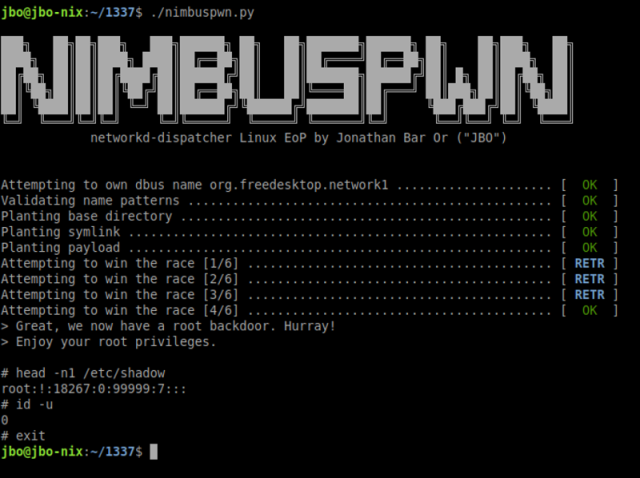
To gain lasting root access, the researcher used the utilization stream to create a back door. The process for this is:
- Copy / bin / sh to / tmp / sh.
- Turns the new / tmp / sh it to a Set-UID (SUID) binary
- Runs / tmp / sh -s. That “-sFlags are necessary as modern shells lose privileges in design.
Microsoft
The proof-of-concept exploit only works when it can use the bus name “org.freedesktop.network1”. The researcher found several environments where this happens, including Linux Mint, where systemd-networkd by default does not own the bus name org.freedodesktop.network1 at startup.
The researcher also found several processes running as the systemd network user, which is allowed to use the bus name required to run arbitrary code from places that can be typed in the world. The vulnerable processes include several gpgv plugins that are launched when apt-get is installed or upgraded, and Erlang Port Mapper Daemon, which allows arbitrary code to be run in some scenarios.
The vulnerability has been fixed in the networkd dispatcher, although it was not immediately clear when or in what version, and attempts to reach the developer were not immediately successful. People using vulnerable versions of Linux should patch their systems as soon as possible.
