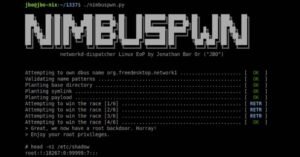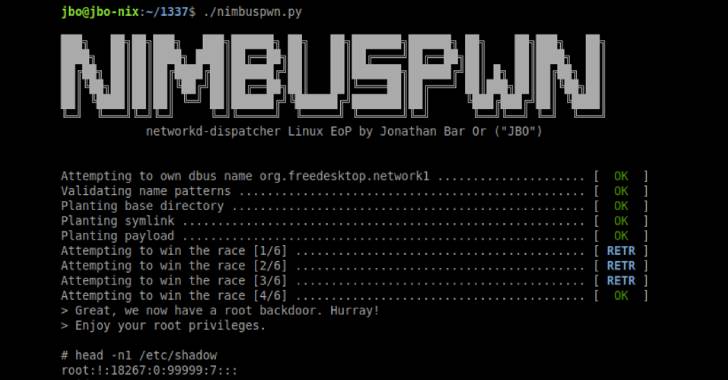
Microsoft on Tuesday unveiled a set of two privilege escalation vulnerabilities in the Linux operating system that could potentially allow threat actors to perform a series of gruesome activities.
Collectively called “Nimbuspwn“bugs” can be linked to gain root privileges on Linux systems, allowing attackers to implement payloads, like a root backdoor, and perform other malicious actions via arbitrary root code execution, “Jonathan Bar Or of Microsoft 365 Defender Research Team said in a report.

On top of that, the defects – traced as CVE-2022-29799 and CVE-2022-29800 – could also weapon as a vector for root access to implement more sophisticated threats such as ransomware.
The vulnerabilities are rooted in a system component called networkd-dispatcher, a daemon program for the network administrator’s system service that is designed to send network status changes.
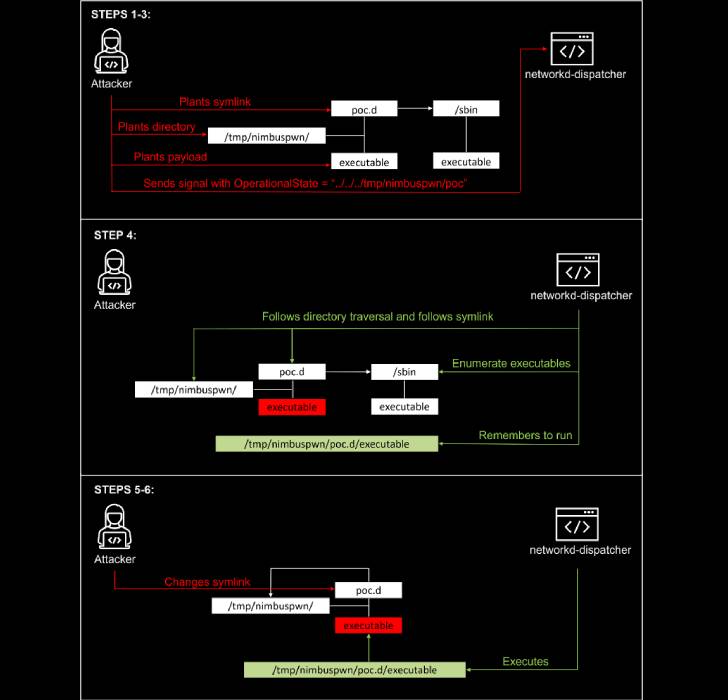
Specifically, they relate to a combination of folder review (CVE-2022-29799), symbolic link (alias symlink) race and check-time to usage time (CVE-2022-29800), leading to a scenario where an opponent with control over a rogue D-Bus service can plant and execute malicious backdoors on the compromised endpoints.

Networkd dispatcher users are strongly advised to update their instances to the latest version to mitigate the potential of exploiting the errors.
“The growing number of vulnerabilities in Linux environments underscores the need for strong monitoring of the platform’s operating system and its components,” said Bar Or.
“This constant bombardment of attacks, spanning a wide range of platforms, devices and other domains, underscores the need for a comprehensive and proactive vulnerability management approach that can further identify and mitigate even unprecedented exploits and problems.”